Cryptography systems and the Merkle tree


Cryptography is one of the core aspects of blockchain and cryptoassets. While cryptocurrencies are relatively new, cryptography has an extensive history. Here’s what encrypted information means and the cryptographic hash function that has been chosen for the operation of many cryptocurrencies.
Cryptography is a technique that seeks to encode messages so that they are unintelligible to everyone except for the official recipients of these messages. The word “crypto” stems from the Greek work “kryptos”, meaning hidden.
Cryptography has seen many uses throughout the course of history. In the Roman Empire, Julius Caesar used what is now known as the “Caesar cipher” to inform his generals of his battle plans. The Caesar cipher involves shifting the alphabet by a number of “positions” and then applying this by equivalence.
For example, according to the Caesar cipher:
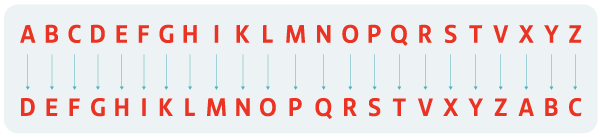
This way you could write “Hello everyone” as “Lhoor hzhvbrqh”.
Cryptography was also used in World War II, albeit in a somewhat more sophisticated way. Germany developed a cryptography system (cryptosystem) whose cipher changed daily, using a rotor engine to encrypt and decrypt messages, known as Enigma machines. British mathematician and cryptographer Alan Turing managed to decipher the code using a combination of Enigma machines, called Bombe machines. Encryption was already something done by computers. The film The Imitation Game explores this story.
The cryptography used by blockchain networks, such as that used by the Bitcoin protocol, is impossible to decipher nowadays. Specifically, Bitcoin uses the hash encryption method SHA-256. The SHA cryptography system was developed by the US National Security Agency (NSA). It involves converting an inbound message, no matter how long it is, into an outbound message of a fixed size. For SHA-256, the size of the outbound message is always 256 bits. Its main characteristics are:
- Deterministic. No matter how many times you try, the same inputs always offer the same output.
- Fast computing. The hash function must quickly return the hash from the input.
- Impossible to decipher. It is impossible to know the inputs from the hash.
- Small changes in the input result in significant changes in the hash.
- Two different inputs will never give the same hash.
You can take a look at a hash calculator here:
Merkle tree: What is it?
Using this information encryption system, information is recorded in the blockchain, resulting in a chain of blocks. Each block contains information that, for Bitcoin blockchains, represent transactions carried out using that cryptoasset. You can think of the hash derived from encrypting a block's information as a kind of ID number or identifying name for that block.
Each block builds upon the foundation of the previous block, so the information contained in one block also includes the information from the previous block. This is known as the Merkle Tree and this is what makes blockchain irreversible. Modifying one block added to the chain involves modifying all the subsequent blocks upon which the blockchain was built.
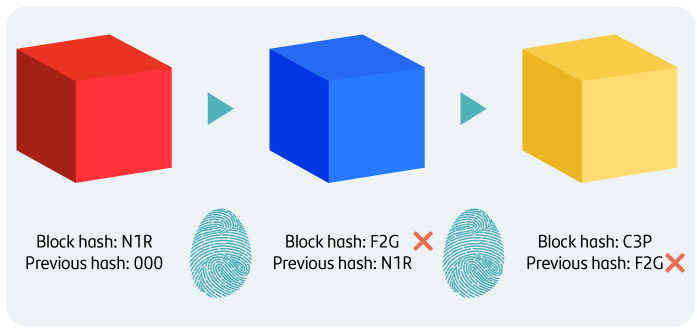
The energy consumption involved in the mining work through which blocks are added to the chain is the main deterrent against modifying information stored in the blockchain.
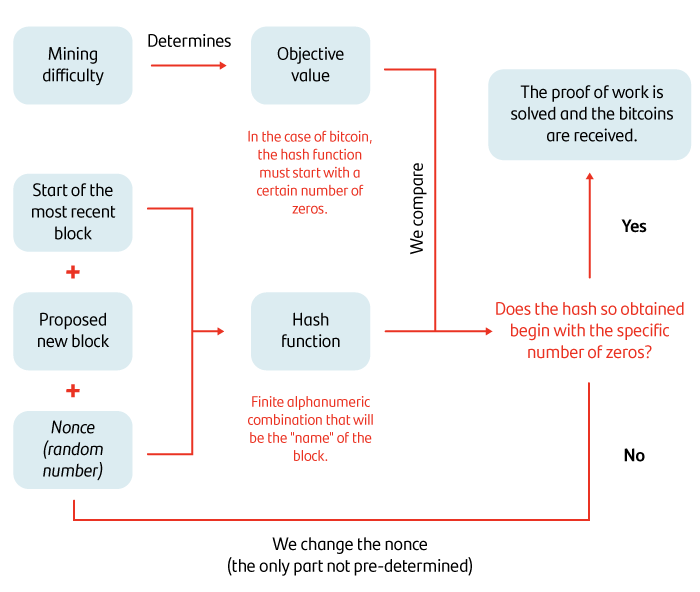
Bitcoin, for example, uses proof-of-work mining. A mining difficulty is set, which, in this case, is that the hash resulting from encrypting the block information starts with a set number of zeros.
To get this hash, you include the information from the previous block, the new block proposed and a "nonce" (a random number that can only be used once in an encryption communication). Bear in mind that this last element is the only random and, as such, varying, element in this process.
Once the final hash has been obtained, you must check whether it complies with the mining difficulty (whether the resulting hash starts with the required number of zeros). At this point, two things can happen:
- The mining difficulty is met, meaning that the proof of work is solved, the proposed block is added to the chain and the miner who undertook the work is rewarded with a new issue of coins determined by the protocol.
- The proof of work is not met, meaning that the nonce must be changed until the required number of zeros is achieved.
This work is labour-intensive, time-consuming and energy-consuming. The deterrent to attempting to modify the information written in the chain is therefore completely understandable.
Bitcoin mining process based on proof of work
As you can gather from this article, encryption is a basic feature of blockchain technology that is used to protect information, but it is only a more evolved system compared to other systems used in the past.The incentive scheme introduced for consensus validation is a key difference.
This article is for educational purposes only and does not reflect the opinion or strategy of Banco Santander, and in no way should be considered as financial advice.
Note: Cryptoassets are exposed to high risk of illiquidity and full loss or temporary unavailability of the capital invested, as they are highly speculative products that see highly volatile prices and huge fluctuations in value. Cryptoassets are unregulated and may not be suitable for retail investors. Their prices are set in the absence of mechanisms to ensure their correct formulation, such as those that exist in regulated stock markets. On a similar note, their high dependence on technology can give rise to operational faults, cyberthreats and risks arising from holding cryptoassets under the applicable legal framework, and credentials or passwords can be stolen or lost. Cryptoassets also entail the risk of fraud or money laundering. This means that cryptoassets may not fall under EU regulations and would therefore be unprotected, meaning that the capital invested may not be covered by the Deposit Guarantee Fund or the Investment Guarantee Fund. Any potential issues may, therefore, be rather costly to resolve.







